JWT Encoder/Decoder
Select encoding or decoding, choose an algorithm, provide the key, and get your result instantly.
Introduction
Our JWT Encoder/Decoder simplifies the handling of JSON Web Tokens (JWTs), offering seamless encoding and decoding functionalities. With support for various algorithms, including symmetric and asymmetric options, users can securely convert payloads into JWT format and decode JWTs to access their original content swiftly. Whether verifying signatures for enhanced security or decoding without verification for quick data retrieval, our user-friendly tool streamlines authentication and authorization processes. Experience efficient JWT management and seamless integration into your applications with our versatile Encoder/Decoder.
What is JWT Encoder and Decoder?
JWT encoder and decoder is a user-friendly tool for encoding and decoding JWT (JSON Web Token) data. JWT serves as a secure method for transmitting JSON data by signing it with a designated key. Our tool enables you to debug JWTs online, offering functions to sign a JWT with a signing key or private key, verify a JWT with a signing key or public key.
With support for 3 algorithms—HS256, HS384, and HS512—you can choose the method that best fits your needs. HSxxx algorithms operate with a single signing key as a string. If a single key is used for both encoding and decoding, it’s termed a symmetric algorithm.
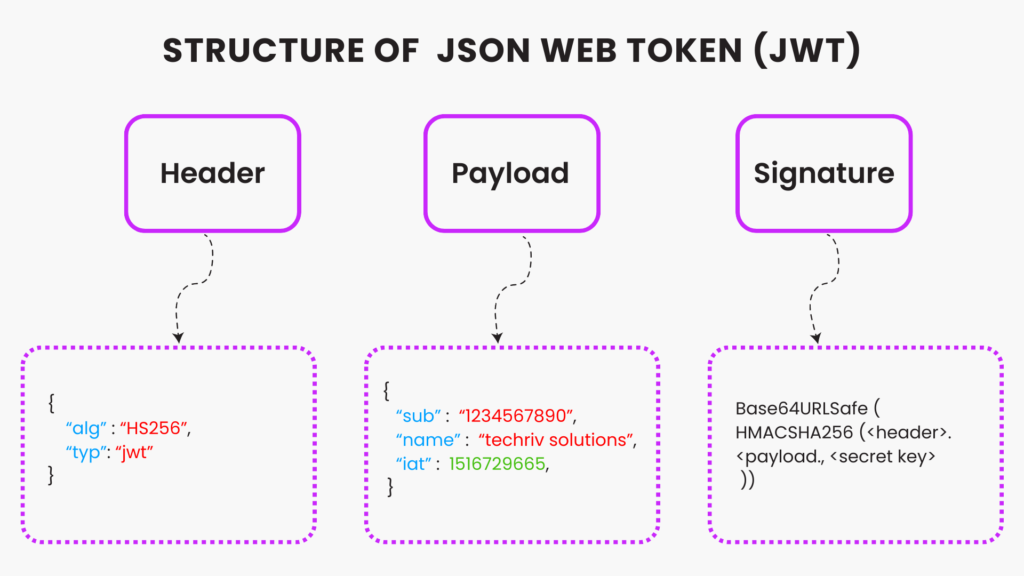
JWTs consist of three parts—header, payload, and signature—separated by dots and encoded in base64 format. The header and payload are accessible to everyone after decoding, while the signature is crucial for secure data transmission. During data transfer between server and client, the signature is used for verification.
While not mandatory, JWTs commonly include predefined claims like “iss” (issuer), “exp” (expiration time), “sub” (subject), and “aud” (audience) within the payload, enhancing data definition and validity. Metadata such as the algorithm used is stored in the header section.
When decoding JWTs, you have the option to verify the signing key or not. Even if the signature is invalid, you can still access the payload and header of the JSON web token.
For HSxxx (symmetric) algorithms, it’s recommended to use secure signing keys of 256 bits (32 characters), 384 bits (48 characters), 512 bits (64 characters), or longer. This precaution helps prevent the cracking of signing keys through brute force methods, enhancing overall security.
Structure of a JWT?
A JWT comprises three essential parts:
Header:
It includes the signing algorithm utilized and specifies the token type, typically “JWT”.
Payload:
This section holds the claims or JSON object data.
Signature:
Generated through a cryptographic algorithm, it verifies the integrity of the JSON payload, ensuring secure data transmission and authentication.
Why is a JWT encoder and decoder tool important?
JWT (JSON Web Tokens) encoder/decoder tools are crucial for several reasons:
Secure Data Transmission: JWTs provide a secure method for transmitting data over networks. Encoder/decoder tools ensure that data is encoded securely and can be decoded only by authorized parties.
Authentication and Authorization: JWTs are commonly used for authentication and authorization in web applications. Encoder/decoder tools help generate JWTs during authentication and decode them to validate user access rights during authorization processes.
Versatility: JWT encoder/decoder tools support various algorithms and configurations, allowing developers to tailor JWTs to their specific security requirements and application needs.
Efficiency: These tools streamline the process of encoding and decoding JWTs, saving developers time and effort in implementing authentication and authorization mechanisms.
Debugging: Encoder/decoder tools serve as invaluable debugging aids, allowing developers to inspect JWTs during development and troubleshoot any issues related to encoding, decoding, or token validation.
How to use JWT Encoder/Decoder?
Follow these simple steps to effortlessly encode or decode your tokens:
Choose Encoding or Decoding: Select whether you want to encode or decode your JWT.
Select Algorithm: Pick from our available algorithms, including HS256, HS384, or HS512, which will be used for generating or decoding your JWT.
Provide Signing Key: If encoding, enter your signing key. If decoding, paste your JWT into the input field.
Initiate the Process: Click the Encode or Decode button, based on your selection, to kickstart the operation.
Retrieve the Result: Access the outcome of the operation in the output field. For encoding, you’ll receive the generated JWT. For decoding, you’ll see the decoded payload and header.
With these steps, you can efficiently encode or decode JWTs using your preferred algorithm, ensuring robust authentication and authorization mechanisms for your applications.